„We were in the zone. We’d done this before.“
On Wednesday, an anonymous hacker (or hackers) stole $32 million worth of ethereum’s cryptocurrency, ether, from three multi-signature wallets thanks to a vulnerability in the contract for the wallets.
A volunteer group of coders calling themselves the White Hat Group took it upon themselves to „rescue“ the funds in the other 500 vulnerable wallets before the hackers could get them. They did this by breaching the wallets using the same vulnerability as the hackers and funneling the funds into the group’s own account.
By Monday afternoon, tens of millions of dollars worth of tokens and ether had been returned to their owners. They say they plan to give all the funds back to their owners by July 31st.
This is the story of how it all happened.
Alex Van de Sande didn’t know what he was in for.
As an interface designer for the Ethereum Foundation, the organization that leads protocol development for the eponymous cryptocurrency and app platform, he was a notable attendee at an annual ethereum workshop at Cornell University that kicked off on Monday. The last time de Sande attended, in the summer of 2016, the worst hack in ethereum’s short history had just occurred: Hackers exploited a bug in the code of a crowd-directed investment fund called the DAO and stole $53 million worth of ether, the platform’s currency.
In response, de Sande became the public face for an ad hoc group of coders who called themselves the Robin Hood group. They exploited the same bug that the hackers had used to siphon away most of the remaining ether from the DAO before the hackers could. It was an extremely controversial move, robbing people for „good,“ before a hard fork split ethereum into two versions and wiped out the effects of the DAO hack on the new version.
Thinking the developer had meant the Ethereum Foundation, the room scrambled to find out what was going on, de Sande told me in an interview. They quickly discovered that the foundation’s wallet had all of its funds intact, but a vulnerability in a popular ethereum client called Parity had let hackers treat multi-signature wallets created with the latest version of the client as personal ATMs.
Multi-signature wallets are popular among companies because they have multiple key-holders and require a majority to sign off on transactions. The hackers cleaned out three of these accounts to the tune of $32 million worth of ether.
„It wasn’t affecting us directly, but we could see that 500 other wallets could be affected, and a few of them were holding more than one million dollars,“ de Sande told me on a phone call from New York. „That’s when we got really worried. We were talking, and a few people said, ‚Our money is safe but somebody can attack these other wallets at any moment. And somebody has to do something about it.'“
The online group of high-profile ethereum developers, which included Taylor Monahan, founder of popular ethereum wallet MyEtherWallet, was hard at work pinning down the problem and formulating a solution.
„Everyone simply does what they can to contribute, which turns out to be immensely powerful,“ Monahan wrote in an email. „Someone says, ‚we need X info‘ and someone else responds ‚on it‘.“
Eventually a plan coalesced. Someone could sweep all of the funds from vulnerable wallets into a secure address and give the ether back to its rightful owners later. Basically, hacking people’s wallets themselves.
But who would push the button? Who would take the risk of running afoul of federal laws on criminal hacking, even if they were supposedly fighting the good fight? Hell, who could be trusted to hold on to that much ether and actually give it back?
Enter the White Hat Group. These are the people who would ultimately „save“ $85 million worth of ether, and even more in the digital assets known as tokens, by taking a page from the hackers‘ own playbook.
The White Hat Group, apparently a volunteer collective of coders, has its origins in the aftermath of the DAO hack that occurred in the summer of 2016.
After hackers took advantage of a bug of the DAO’s code to siphon away $53 million worth of ether, de Sande formed a small group of ethereum developers to hack back and rescue the remaining ether in the DAO by siphoning it out into a „white hat“ account. They called themselves the Robin Hood group, and it worked.
But then, the unexpected happened: Vitalik Buterin, ethereum’s inventor and chief scientist of the Ethereum Foundation, elected to split ethereum into two versions in order to completely wipe out the damage the DAO hackers had done. On the new version of ethereum, it was as if the hack had never happened. On the old one, called ethereum classic, nothing had changed—the hackers still made bank.
The White Hat Group formed to take over where the Robin Hood group had left off, and siphoned off the ether classic left in the shadow DAO by exploiting the same bug as the hackers. The person acting as the public face of the White Hat Group at the time was „jbaylina“ on Reddit, the online pseudonym of a coder named Jordi Baylina, according to de Sande. They then set about returning the funds to their owners.
Fast forward to 2017, and the recent hack due to the vulnerability in multi-signature wallets created with a popular client called Parity. The ethereum community was looking to sweep vulnerable wallets of all their funds before the bad guys could get to them.
„We were in the zone. We’d done this before“
„We had just finished a two-day product meeting for Giveth, and that momentum was just fucked,“ Green said over video chat from their office in Spain. „We had no other options, really. It was trivial for these funds to be taken from anybody else.“
When reached for comment over Reddit, Baylina directed Motherboard to Green.
According to Green, all of the developers who had gathered in the Giveth office for the meeting got to work writing a script to sweep all the remaining funds from the vulnerable wallets. However, Baylina, Green, and a hacker who goes by the name „Barry Whitehat“ were „the main three“ members of the White Hat Group, Green said.
„We were in the zone,“ he said. „We’d done this before. We did this for the DAO. Last time, we were all spread apart. We were really lucky to be in the same place this time.“
Later that night, Baylina posted on Reddit that the White Hat Group had funneled $85 million worth of ether and $100 million in tokens from vulnerable wallets and stashed it in a secure address they controlled. The group will create new wallets for those affected and return their funds, Baylina wrote, and cryptographically proved that he owns the account containing the funds. The White Hat Group will not be accepting donations for their work, Baylina wrote.
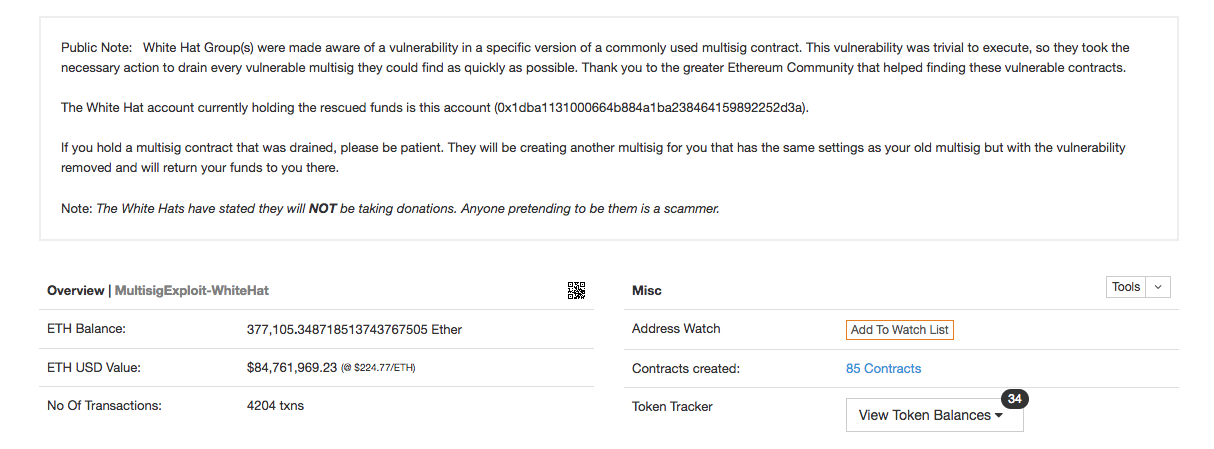
„In the end, [the White Hat Group] were the ones pushing the button because they are trusted, and they have the courage,“ de Sande said. „But they had a lot of help from the community as a whole.“
Monahan, of MyEtherWallet, also emphasized how the entire community—not just the core White Hat Group—had contributed to the effort.
Together, the group managed to scrape together $208 million in ether and tokens, the assets that are issued during ICOs.
These funds included the entire contents of a „reserve“ wallet for BAT, the tokens issued during the wildly successful ICO for a privacy-boosting internet browser called Brave, worth nearly $50 million. These tokens were supposed to be used to incentivize new users to join the platform, according to an announcement posted by BAT after the hack.
„So far we see good intentions only from [White Hat Group],“ Brave founder Brendan Eich wrote me in a direct message over Twitter on Monday morning. „We are working with them now and expect full recovery.“
Hours later, he messaged me again: „FYI we got the tokens back.“
It’s possible that the White Hat Group members, aside from Green and Baylina, wish to stay relatively anonymous because hacking, even if it’s for „good,“ is illegal under federal law.
„If I were advising someone, I would say not to do it—it’s very risky,“ Marcus Christian, a DC-based partner specializing in cybersecurity at law firm Mayer Brown, told me over the phone. „It’s going to be a crime under the law and the only question is if anyone is going to prosecute it or not. That’s not a good place to be.“
De Sande didn’t appear to be worried for the White Hat Group on this point. „If you see a burning building and you break in to save the cat that’s inside, I don’t think anyone will press charges against you for trespassing,“ he said. „I don’t think any judge in their right mind would think it’s a valid trespassing case.“
According to Green, the team is mostly worried about desperate people who learn of the group’s temporary wealth coming after them.
„We have a bat,“ he said over video chat. „We’re careful about where the cameras are going. It’s a new office, and we have no address. Jordi isn’t sleeping at home.“
That aside, it seems like the White Hat Group has little to fear from most of the ethereum community.
„I am extremely grateful the White Hat group responded as they did,“ Matthew Carano, a spokesperson for Swarm.City, one of the three companies that had all its ether stolen by the hacker, wrote in an email, „and believe if you [polled] every group whose funds were saved, they would say the same thing.“
The BAT organization doesn’t seem to be incensed, either.
„I’ll just say the [White Hat Group] came through, they are good folks,“ Eich, of BAT, wrote me in a Twitter direct message. „Remember near the end of ‚The Dark Knight,‘ ‚clowns and hostages?‘ Batman has to sort out very quickly who was who and save the hostages. [White Hat Group] is Batman.“
It’s important to keep in mind, though, that these comments were made in the afterglow of a seemingly successful rescue operation.
The amount of funds in ether and tokens in the White Hat Group’s account has only gone up over the past week—$200 million is nothing to sniff at, and people want their virtual money back.
Source: How Coders Hacked Back to ‘Rescue’ $208 Million in Ethereum – Motherboard

